Compliance isn't just a checkbox — it's a critical business function that affects everything from operational risk to customer trust. For development teams, balancing compliance requirements with velocity can be particularly challenging. GitLab's Custom Compliance Frameworks offer a powerful way to integrate compliance verification directly into your development workflow. In this article you'll learn what they are and how to use them for maximum efficiecy.
What are GitLab Custom Compliance Frameworks?
GitLab Custom Compliance Frameworks allow organizations to define, implement, and enforce compliance standards directly within their GitLab instance. This feature extends GitLab's built-in compliance capabilities by enabling teams to create customized frameworks that align with specific regulatory requirements, internal policies, or industry standards.
Custom Compliance Frameworks have the following benefits:
- Reduce manual tracking
- Accelerate audit readiness
- Enforce compliance controls natively

With this release, more than 50 out-of-the-box (OOTB) controls are provided (with more coming soon) that can be tailored to your organization's unique compliance needs, including HIPAA in healthcare, GDPR for data privacy, SOC2 for service organizations, or industry-specific regulations. Some examples of OOTB controls include:
- Separation of duties (e.g., at least two approvers and author approved merge request)
- Security scanners running (e.g., SAST running and Dependency Scanning running)
- Authentication/authorization (e.g., project visibility not public and AuthSSO required)
- Application configuration (e.g., status checks required and Terraform required)
Additionally, you can configure external environmental controls using the GitLab API to check the status and details of an external environment.
Creating a Custom Compliance Framework from scratch
Now that we understand the value, let's explore how to implement Custom Compliance Frameworks in your GitLab environment. We will use this demo application and you can follow along in this video.
Note: A GitLab Ultimate subscription is required.
Step 1: Define your compliance requirements
Before building your custom framework, you need to clearly define your compliance requirements:
- Identify applicable regulations: Determine which regulations and standards apply to your organization (e.g., GDPR, PCI DSS, and HIPAA).
- Map requirements to controls: Break down each regulation into specific, actionable controls.
- Prioritize requirements: Focus on high-risk areas and requirements with the greatest impact.
Step 2: Create your Custom Compliance Framework
To create a custom compliance framework in GitLab:
- Navigate to your GitLab group's Secure > Compliance Center section.
- Press the New framework button.
- Select Create blank framework.

- Provide a name, description, and color for your framework.
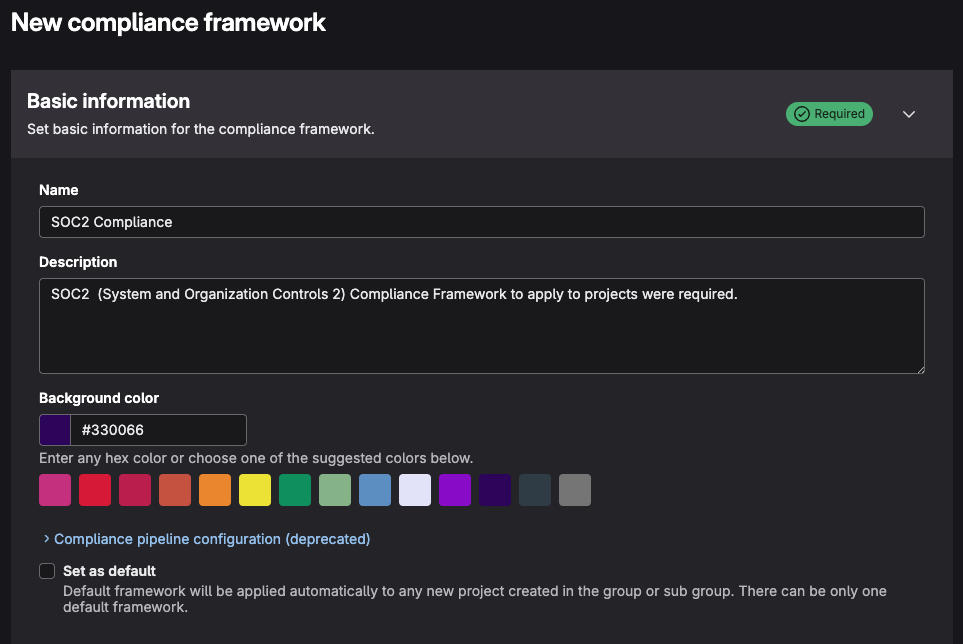
-
Add a requirement to the framework:
a. Scroll down to the Requirements tab.b. Press the New requirement button.
c. Provide a name and description.
d. Under the Controls section, select Choose a GitLab control.
e. Select a control from the list (e.g., at least two approvals, SAST running).
f. Press the Create requirement button.

- Press the Create framework button.
The framework will be created as specified and will now be available to add to projects. Additionally, compliance frameworks can be imported using a JSON with the appropriate schema.
Step 3: Apply the framework to projects
Once your framework is created:
- From the Compliance Center, select the Projects tab.
- Use the search bar to Search or Filter results.
- Select the project(s) you wish to apply your framework to.
- Press the Choose one bulk action button.
- Select Apply frameworks to selected projects.
- Press the Select frameworks button.
- Select your framework(s) from the list.
- Press the Apply button.

The framework will now be applied to the project, making its requirements visible and trackable.
Step 4: Monitor and report on compliance
With your framework in place, you can now:
- Use the Compliance Center to track compliance status across projects including details and suggested fixes for failed controls.
- Generate compliance reports for audits and stakeholder reviews.
- Set up compliance alerts to notify stakeholders of potential compliance issues.
- Review audit events to overview action taken on compliance settings.

Real-world example: Implement a SOC2 compliance framework
System and Organization Controls 2, better known as SOC2, is a rigorous auditing standard developed by the American Institute of Certified Public Accountants that assesses a service organization's controls related to security, availability, processing integrity, confidentiality, and privacy. You can read my Guide to fulfilling SOC 2 security requirements with GitLab to learn more.
Now, let's review a practical example of using a Custom Compliance Framework to verify SOC2 security compliance, which requires:
- implementation of controls to protect against unauthorized access
- establishment of procedures for identifying and mitigating risks
- setting up systems for detecting and addressing security incidents
Disclaimer: This is only an example showcasing some of the controls possible for adhering to SOC2. Be sure to consult with your security/compliance team before moving any implementation to production.
A Custom Compliance Framework for SOC2 will look as follows using some GitLab OOTB controls:
- Name: SOC2 Security Requirements
- Description: Adds the security requirements for SOC2 framework compliance
- Requirements:
- Implement controls to protect against unauthorized access
- Auth SSO enabled
- CI/CD job token scope enabled
- Require MFA at org level
- Establish procedures for identifying and mitigating risks
- At least two approvals
- Author approved merge request
- Committers approved merge request
- Default branch protected
- Setting up systems for detecting and addressing security incidents
- Dependency Scanning running
- SAST running
- DAST running
- Implement controls to protect against unauthorized access
When applied to your project(s), this framework allows you to oversee if/and when they fall out of compliance and what can be done to bring them back into compliance. Note that you can create and apply multiple compliance frameworks to a project(s). For example, you can have one for SOC2 process integrity requirements.
Implement security policies to ensure compliance requirements are met
Although not required, security policies can be applied to projects containing a Custom Compliance Framework. This allows you to assure that certain compliance criteria will be enforced via security policies. For example, you can force security scanners to run on projects that contain a Custom Compliance Framework requiring security scanning.
GitLab provides various different security policies:
- Scan execution policy: Enforces security scans, either as part of the pipeline or on a specified schedule.
- Merge request approval policy: Enforces project-level settings and approval rules based on scan results.
- Pipeline execution policy: Enforces CI/CD jobs as part of project pipelines.
- Vulnerability management policy: Automatically resolves vulnerabilities that are no longer detected in the default branch.
Let’s go ahead and force a SAST scanner to run in order to automatically adhere to any requirements that require SAST scanning. To create a security policy and apply it to a project with a particular framework:
- Navigate to a project that has a Custom Compliance Framework requiring SAST scanning.
- In the sidebar, select Secure > Policies.
- Press the New policy button.
- Under Scan execution policy, press the Select policy button.
- Fill in the Name and Description.
- Under Actions, select SAST as the scan to run.

- Under Conditions, select the pipeline to be triggered when a pipeline runs for all branches.

- Press the Configure with a merge request button.
- An MR is now created in a separate project containing all the security policies scoped to this project.
- Press the Merge button.
Now SAST will run for every branch, assuring you are compliant in that area. Be sure to review all the different types of security policies and see how they can suit your requirements.
5 best practices to follow
To maximize the value of Custom Compliance Frameworks:
- Start small: Begin with one critical regulation or standard before expanding.
- Involve key stakeholders: Include compliance, security, and development teams in framework creation.
- Automate where possible: Use GitLab CI/CD to automate compliance checks.
- Document thoroughly: Maintain clear documentation of how your framework maps to regulatory requirements.
- Review regularly: Update your frameworks as regulations evolve or new requirements emerge.
Get started today
GitLab Custom Compliance Frameworks represent a significant advancement in DevSecOps by bringing compliance directly into the development workflow. By implementing custom frameworks, organizations can reduce compliance overhead, improve risk management, and accelerate development cycles while maintaining robust compliance with regulatory requirements.
The ability to define and enforce Custom Compliance Frameworks gives teams the flexibility they need to address their specific regulatory landscape while providing the structure necessary to ensure consistent compliance practices across the organization.
As regulatory requirements continue to grow in complexity, tools like GitLab Custom Compliance Frameworks will become increasingly essential for organizations looking to balance compliance requirements with development velocity in a sustainable way.
To try Custom Compliance Frameworks today, sign up for your free, 60-day trial of GitLab Ultimate.
Learn more
Visit these resources to learn more about Custom Compliance Frameworks and how they can benefit your organization:



